App Delivered
Client Satisfaction

Secure tracking systems and prevent disruptions in global delivery networks.
Protect patient data and ensure full compliance with healthcare regulations.
Safeguard financial transactions and defend critical payment infrastructures.
Keep student records and learning portals protected from unauthorized access.
Secure online payments, user data, and third-party integrations end-to-end.
Protect production systems and internal networks from cyber intrusions.
Secure mobile devices and remote connections for distributed teams.
Protect digital platforms, listings, and client records from potential threats.
Ensure booking systems and customer data remain safe and private.
Implement access controls and monitoring to prevent unauthorized exposure.
Can’t find your industry? We’ll secure your systems wherever your business operates.

Evaluate systems thoroughly to identify and eliminate vulnerabilities.

Ensure uninterrupted operations with reliable recovery procedures.

Maintain full adherence to all relevant security standards.
For over years, CortechDev has helped businesses move from patchwork systems to purpose-built software proven across 100+ successful deployments.
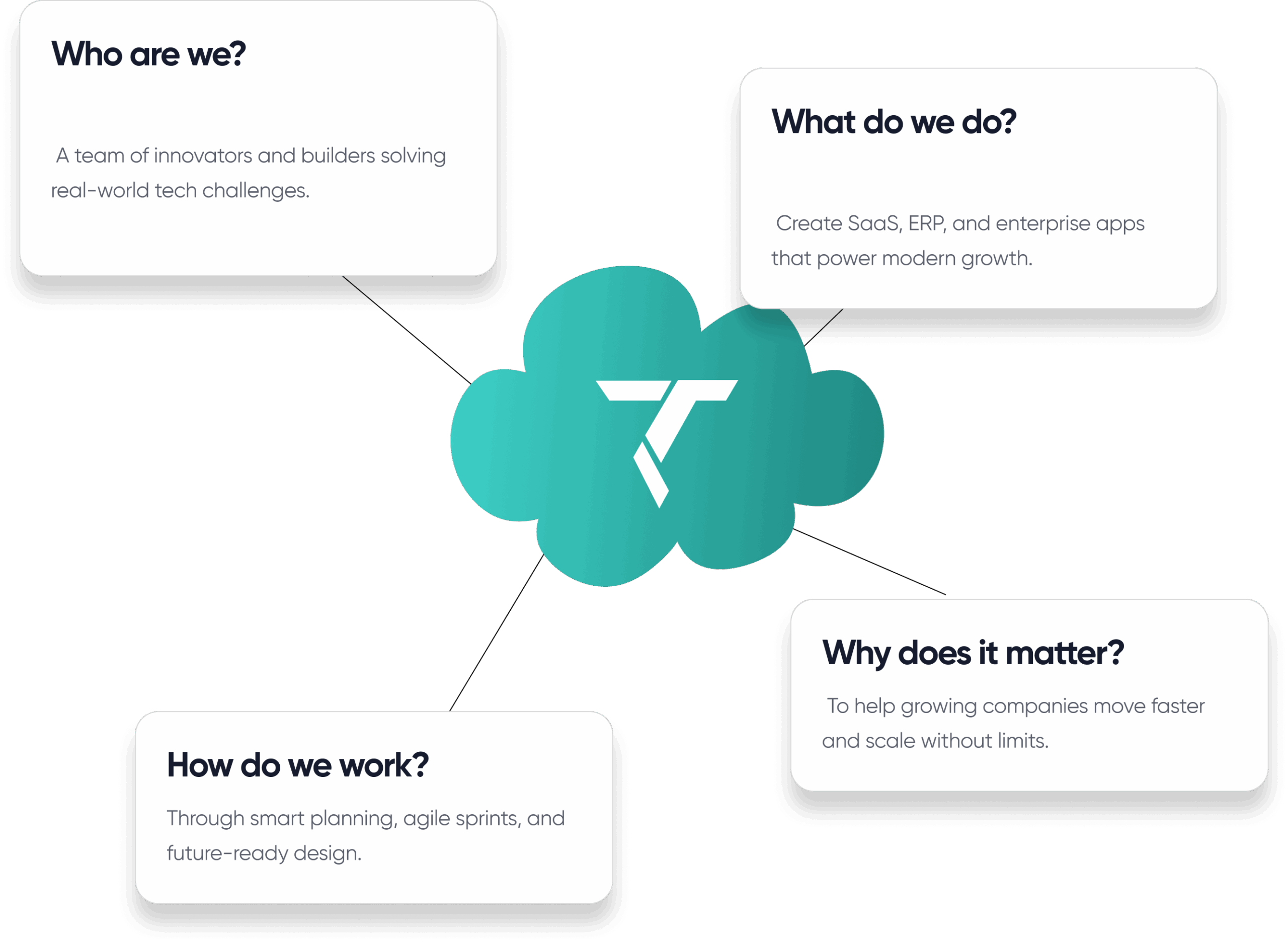

Uptime
Systems built for stability and scale.

Integrations
Your tools, data, and workflows — unified.

Secured
Solutions that evolve with your business.

Efficiency
Fast, optimized, and built to last.
Our services are designed to reduce complexity, improve performance, and keep your business ready for what’s next.

Find vulnerabilities and build a security roadmap that fits your operations.

Design and implement secure, scalable frameworks that guard all connections.

Protect cloud environments with custom access controls and encryption.

Ensure full compliance with all global data security and privacy standards.

Detect potential breaches in real time and respond quickly before damage is done.

Control everyone who gets access to what — both securely and efficiently.

Keep every device in your network safe from internal and external threats.

Secure your information with advanced encryption and data management.

Empower your team to recognize, avoid, and report potential cyber threats.
We build products that solve real problems and create real results. Here’s a look at the projects we’ve designed, developed, and launched with our clients.

Graphic Design

Graphic Design

Graphic Design

Graphic Design
Protection you can trust — expert security strategies that defend your systems, data, and reputation against evolving threats.
We identify vulnerabilities before attackers do and create plans to secure every entry point.
We ensure your business meets GDPR, HIPAA, and ISO standards without any hassle.
We prioritize the right investments and eliminate wasteful spending on ineffective security.
Our strategies include continuous surveillance to detect and respond to threats in real time.
We prepare your team to act quickly and minimize damage when security events occur.
Our consulting builds a security culture that evolves with new threats and business changes.
We work across a trusted stack of frontend, backend, cloud, and data technologies; we are flexible enough to adapt to your preferred stack.













The size, features, and overall goals of your project.
The depth of integrations, tech stack, and performance requirements.
How fast you want to launch and the team size required to make it happen.
Trusted by teams who count on us to uncover the real challenges and deliver software that actually solves them.

CortechDev understood our challenges from day one. They built a platform that actually works the way property owners think — everything is organized, simple to manage, and reliable.
Chris Amani
Property Tools

The team at CortechDev went beyond just development — they truly understood our mission. The AI experience feels intelligent yet compassionate, helping users naturally improve their mental well-being.
Dragan Alexander

From concept to launch, CortechDev delivered exactly what we needed. The system runs smoothly, our customers find it easy to use, and their support has been exceptional throughout.
Chris Percival
Got questions? You’re not the only one here are some things clients ask us all the time.
Yes, we do. Our in-house cybersecurity and IT consulting teams operate across multiple time zones. Most of our specialists work in GMT+5, but we align our schedules with your business hours — ensuring live collaboration and quick response when needed.
Our pricing depends on your organization’s size, infrastructure, and security goals. Whether you need a full security assessment, compliance review, or long-term consulting support, we provide upfront estimates with clearly defined deliverables — no hidden fees or generic pricing.
Because we take a prevention-first approach. Our in-house team focuses on identifying risks before they become threats, improving your defenses, and aligning your systems with international security standards. We help you build a secure foundation that supports business continuity.
Our security consultants work with ISO, NIST, CIS, and GDPR frameworks daily. From vulnerability assessments and risk audits to compliance planning, our in-house team has secured systems across industries, including finance, healthcare, and SaaS — all without outsourcing.
Your project is managed entirely by our in-house consultants, engineers, and project managers. We plan, test, and implement every step under one roof — ensuring consistent communication, accountability, and a clear understanding of your organization’s security posture.
We follow strict data-handling protocols and NDAs for every engagement. All assessments are conducted by our internal team — no third parties. Sensitive data is encrypted, stored securely, and accessed only by authorized personnel, maintaining full confidentiality throughout the process.
Share your challenge, and we’ll find the smartest way to solve it.